Introduction
Before one can leverage artificial intelligence (AI) and machine learning (ML) for multi-domain operations (MDOs) as part of Joint All-Domain Command and Control (JADC2), one must do the grunt work of laying an “information foundation.” Laying this foundation—in which data are tagged, securely stored and transported, and easily accessible—requires the mundane and ongoing work of organizing and safeguarding all the information the military needs for C2 across domains, services, and echelons. This same body of information will be the input for AI and ML algorithms. Absent such an information foundation, little progress can be made.
Although recent successes in AI/ML have been encouraging in the field of gaming, employing similar techniques for some C2 functions will remain challenging given the real-world barriers of incomplete information, poor data quality, and adversary actions. Other AI/ML techniques, such as those for predicting the status of aircraft in theater, will be more readily applicable. Reaching JADC2 goals will depend on both identifying the C2 needs of core military mission sets and establishing software development plans that are achievable in the near and far terms.
The remainder of this paper describes the need for JADC2 with embedded AI/ML, offers a cautionary note about the lure of AI/ML, outlines the AI/ML barriers to overcome, and suggests a path forward. In general, investments in people and resources will be needed to move beyond today’s man-power intensive C2 paradigm. Improving upon current planning processes with automation and some AI/ML is a realistic goal that is worthy of working toward.
Given the increased complexity of MDO planning, the reduced timescales, and the greater data requirements, military planners will require new tools, including those based on AI/ML.
Sherrill Lingel
The Need for JADC2 in Support of MDO
Modern warfare has expanded beyond the traditional domains of land, air, and sea, requiring military commanders and their staffs to plan, command, and control forces not only in these traditional domains but also now in those of space and cyber and across the electromagnetic spectrum. To complicate matters further, activities across all these domains have expanded beyond traditional warfare to shape the competitive environment in which most nations live today—prior to open hostilities. A military must be able to integrate across these domains not only in warfare, but also in competition. Today’s military operations already require resilient and secure means of communicating and sharing data across echelons, domains, organizations, and geographic regions. Tomorrow’s all-domain warfare and competition will place even higher premiums on the scale and speed of access to information, on understanding that information, and on rapid decision-making—key elements of an effective JADC2 capability (Lingel et al., 2020).
However, today’s legacy systems and infrastructure for planning, scheduling, and execution monitoring military missions are incongruent with the modern, all-domain world in which militaries must compete. Given the increased complexity of MDO planning, the reduced timescales, and the greater data requirements, military planners will require new tools, including those based on AI/ML. A proper prioritization of investment in these tools requires an understanding of their capabilities, their barriers, and their potential fulfillment of the emerging C2 needs for MDOs.
The Lure of Artificial Intelligence/Machine Learning (AI/ML)
The appeal of AI/ML stems in part from recent demonstrations of AI/ML systems
achieving super-human performance in increasingly complex games, combined with growing recognition of the operational demands of future high-end conflicts. The recent success of AlphaStar, an AI/ML system trained to play the real-time strategy game StarCraft, hints at future applications of supervised and reinforcement learning for tactical and operational C2.[1] However, significant research is still needed to transition these technologies from gaming to warfighting.
As AI algorithms are developed for real-world, dynamic, multi-domain, large-scale, and high-tempo operations, important metrics will need to be selected, evaluated, and monitored to gauge algorithm performance, effectiveness, and suitability. Key algorithm metrics will include the following: efficiency (the time and memory needed to compute), soundness (whether the algorithm produces valid results), optimality (whether the algorithm provides a best result for a given objective), robustness (whether the algorithm degrades gracefully under unanticipated cases), explainability (whether a human can understand the “why” of the results), and assuredness (whether the algorithm operates as intended) (Walsh et al., 2021).
Because there is no direct application of commercial and academic AI/ML systems to military missions, the technologies will need to be transitioned to a military setting before they can provide an operational advantage. To decide which AI/ML technologies to pursue, the military must first understand the operational demands the technologies will need to support (e.g., air superiority, air defense, tanker support, etc.). The operational demands will then determine the C2 processes (e.g., situational awareness, airspace deconfliction, etc.) needed to enable the operational missions. Understanding the limitations of the AI/ML technologies, particularly the difficulty they encounter in reasoning under conditions of uncertainty, will be equally important.[2] Otherwise, the technologies may fall short of expectations.
All-domain warfare and competition will place even higher premiums on the scale and speed of access to information, on understanding that information, and on rapid decision-making.
Sherrill Lingel
AI/ML Barriers to Overcome
Several barriers to realizing the promise of AI/ML for military applications exist. One barrier is military culture, which is often risk-averse (lives are at risk) in contrast with that of the commercial world, where taking big risks can pay big monetary rewards. A related cultural difference is in sharing data. The military tends to be concerned with securing information (for only those with “the need to know”), whereas the commercial world values open access to data (“sharing widely”) for application development and other monetary benefits. Therefore, it will be important to incorporate security concerns in military software development and information technology (IT) operations—known as DevSecOps—to thwart adversaries and bad actors who might seek to degrade C2 through cyber means. Perhaps one of the greatest challenges not yet fully faced is to ensure the suitability of AI/ML algorithms for real-world military situations in which the “fog of war,” incomplete information, and adversary actions represent distinct contrasts from a gaming environment.
Another barrier is data inaccessibility within the military itself. To move forward, the military will need a unified data management policy and sufficient IT to make large amounts of data accessible to C2 forces to support their AI-assisted decision-making. In other words, there must be an AI ecosystem that supports collecting, tagging, storing, securing, and sharing data. This ecosystem will rely on common data standards, clearly designated authorities, integrity checks, and intrusion safeguards. Cloud computing and data lakes will be key components. A cloud-based data lake can be leveraged for distributed computing, redundant storage, and enterprise-wide connectivity. Building out an environment like this to provide large amounts of data in a secure way across domains and security levels will present challenges for JADC2 given existing military policies, cultures, authorities, budgets, and acquisition paths.
A third barrier is the need to restructure military operations centers and the training of personnel who run them. An increase in machine-to-machine communication, combined with the automation of C2 processes, will likely induce both physical changes and staffing changes in the operations centers, freeing up human operators to engage in more cognitive tasks, such as evaluating and refining potential courses of action. The adoption of AI/ML technologies will create new roles and responsibilities. Operators will need to be trained to manage and navigate the AI ecosystem, all while acting as responsible data stewards to ensure the quality and completeness of the data captured and stored in that ecosystem. Additionally, whereas planners and decision-makers of today are trained to think within a single domain, new roles will likely emerge requiring personnel to be trained to think in multiple domains all at once.
A fourth barrier is the existence of military subcultures. Integrating AI capabilities across just the air, space, and cyber domains even within just one military service may be difficult given the differences in subcultures among operators, the variations in planning timelines, and the dissimilar distributions of authorities for achieving different operational effects. Still, the need for all-domain C2 is pressing and increasingly pervasive. For this reason, all these barriers—military culture, cyber security concerns, algorithms applied to problems with poor knowledge quality, data inaccessibility, operations center restructuring and training, and military subcultures—must be faced and overcome to embed AI applications in JADC2.
Effectively Moving Forward
The picture may appear grim. Many barriers exist, and a pressing need to move forward quickly demands change now. Yet progress can be made if steps toward the goal are broken down into tractable problems and if the military keeps its “eyes wide open” to technological possibilities and limitations alike. The goal should not be complete automation of C2, but rather effective human-machine teaming for C2. The steps toward that end should include, first, the continuous development and prioritization of JADC2 concepts of operation (CONOPs) and, second, the identification of corresponding needs and opportunities for AI/ML augmentation in the enabling C2 processes.
At the same time, it will be necessary to set the conditions for a data-driven AI ecosystem, which means placing weapons systems and related data into multi-domain data lakes for use by those who ought to have access to the data while also applying “zero-trust” and other security principles to ensure resilient and secure management of that data. As AI software applications are developed, it will be necessary to experiment with them in operational test-bed environments, integrate them with C2 systems, and then deploy them to operations centers. There will likely be iterations of capabilities—first putting limited capabilities into operations centers, then generating user feedback, and then rapidly updating the software applications. Analysts and technologists will want to explore CONOPs to facilitate human-machine teaming, build human trust in the AI algorithms, and improve algorithm explainability. Targeted military investments will likely be needed in areas where commercial demand is lower, such as AI
algorithms for learning where data are scarce or for defending against attacks against those very algorithms.
Current AI/ML techniques need data from which to learn. Given the (fortunate) lack of real-world data to inform the refinement of these techniques for war, the military could leverage modeling, simulation, and exercises to generate training data for AI/ML algorithms. Such algorithms could then assist in the development of, for example, weapon-target pairing. Supervised or reinforcement learning algorithms could support this C2 function, akin to the learning algorithms recently applied to commercial games. But military algorithms must also account for uncertainty in real-world situations—a major difficulty for both humans and algorithms.
As the U.S. Air Force Chief of Staff said in August 2020, “Accelerate change or lose.” Making timely progress toward JADC2 is an imperative for modern warfare and doing so “within the competitors’ fielding timelines” (Brown, Jr, 2020) is required. The demand is real but setting realistic expectations for AI/ML is important. There is room for improvement in existing C2 processes with automation and, in some cases, AL/ML; in contrast, other C2 processes will remain hard for both humans and algorithms. As U.S. House Armed Services Committee Chairman and Representative Adam Smith, D-Wash., said of JADC2 in September 2021, “The goal is correct, but do not underestimate the difficulty of achieving it (Harper, 2021).”
Whereas planners and decision-makers of today are trained to think within a single domain, new roles will likely emerge requiring personnel to be trained to think in multiple domains all at once.
Sherrill Lingel
Footnotes
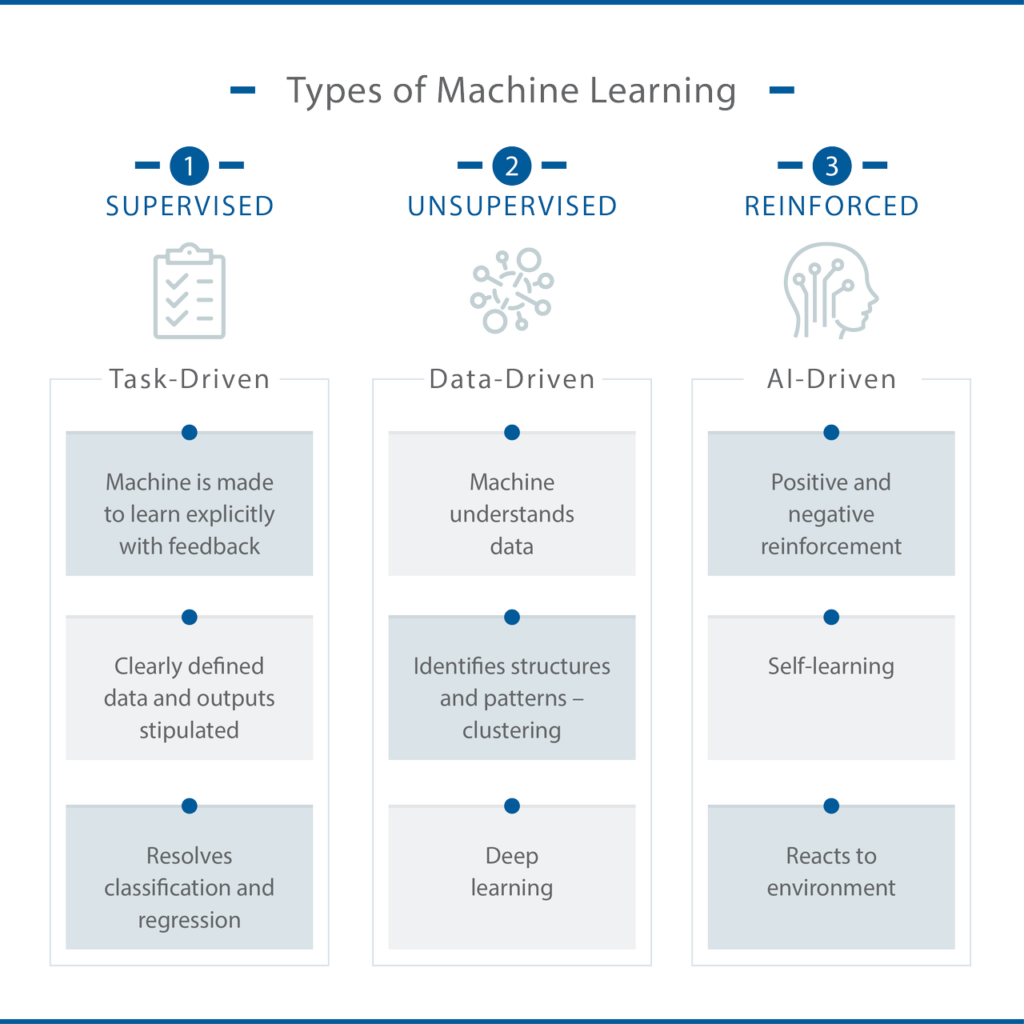
[1] Reinforcement, supervised, and unsupervised learning are three types of ML. Reinforcement learning
algorithms learn from mistakes by trial and error.
[2] Algorithms are challenged by situations where there are: (1) incomplete information; (2) noisy inputs;
and (3) a lack of historical data or a suitable simulation environment to train from.
References
Lingel, S., Hagen, J., Hastings, E., Lee, M., Sargent, M., Walsh, M., Zhang, L.A. and
Blancett, D. (2020). Joint All-domain Command and Control for Modern Warfare: An Analytical Framework for Identifying and Developing Artificial Intelligence Applications. Volume I: Artificial Intelligence Applications for Joint All-Domain Command and Control, Santa Monica, Calif.: RAND Corporation, RR-4408/1-AF.
Walsh, M., Menthe, L., Geist, E., Hastings, E., Kerrigan, J., Léveillé, J., Margolis, J.,
Martin, N. and Donnelly, B.P. (2021). Exploring the feasibility and utility of machine learning-assisted command and control. Volume 1, Findings and recommendations, RAND Report RR-A263-1.
Brown, C. Q. Jr., Accelerate Change or Lose, [online]. (2020). Available from:
https://www.af.mil/Portals/1/documents/2020SAF/ACOL_booklet_FINAL_13_
Nov_1006_WEB.pdf
Harper, J. (2021). Will the Military Waste Billions on JADC2 Efforts?. National Defense [online], September. Available from: https://www.nationaldefensemagazine.org/articles/2021/9/29/will-the-military-waste-billions-on-jadc2-efforts







