Introduction
The U.S. Chairman of the Joint Chiefs of Staff (CJCS) recently testified to Congress about the U.S. military’s new joint warfighting concept (JWC) and the importance of the associated new Joint All Domain Command and Control (JADC2) framework to its realization. Specifically, he stated to the U.S. House of Representatives on June 23, 2021:
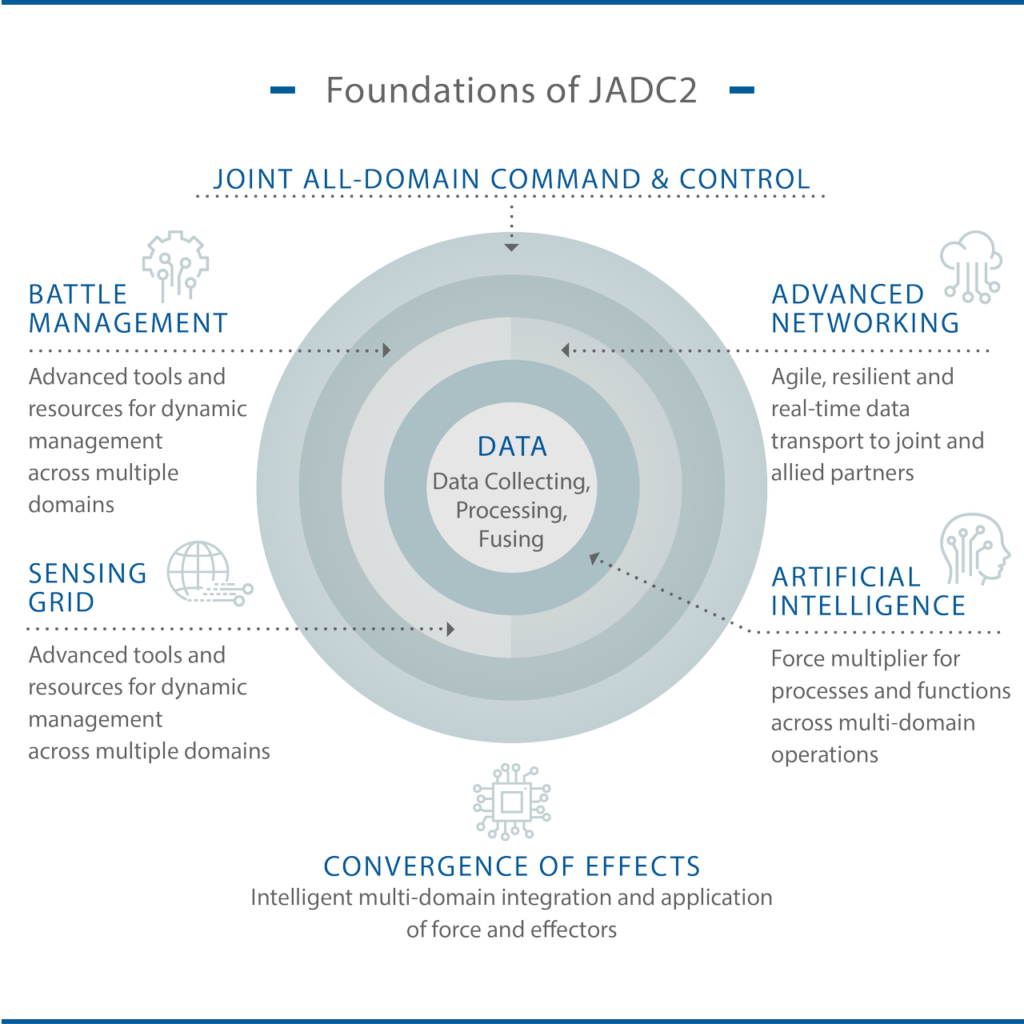
The JWC is a multi-year effort to develop a comprehensive approach for joint operations against future threats and provide a guide for future force design and development. Supporting concepts to the JWC describe key warfighting functions. They are fires, logistics, C2, and information advantage. The Joint All Domain Command and Control (JADC2) framework enables the holistic development and realization of the JWC and Supporting Concepts.
– David Deptula
The fundamental basis of the JWC is the notion of all domain operations. This is the next evolution in the U.S. military’s journey to optimize the synergy of effects that accrues from operating in an integrated fashion across all the domains of air, space, sea, land, and the electromagnetic spectrum. The journey began with the passage of the Goldwater-Nichols Act of 1986 that aimed to improve the ability of U.S. armed forces to conduct joint (interservice) and combined (interallied) operations. If developed and implemented properly, the JWC will yield a far more decisive, powerful set of combat outcomes than today’s “joint” operations that in many cases simply involve service component deconfliction vice integration. For this to happen, the U.S. Department of Defense (DOD) needs to get serious about turning theory into reality. That means taking incremental but concrete steps toward meeting the objectives of JADC2, not waiting for a complete solution before implementing. JADC2 will require much time to engineer as it involves a mammoth conversion of existing concepts, capabilities, and service perspectives. However, accelerating these endeavors can be accomplished through rapid evolution of current command and control paradigms. Specifically, it is time to move beyond large, centralized, static C2 facilities to mobile, distributed C2, with the capability to handle the same volume and diversity of information of a regional combined air and space operations center (CAOC).
As it seeks all domain synergy, embracing complementary vice merely additive employment of capabilities from different domains, the goal of JADC2 is to seek interdependency that enhances effectiveness, and compensates for individual vulnerabilities of each of the domains. Desired military effects will increasingly be generated by the interaction of systems that share information and empower one another. Instead of a set of disconnected, singularly focused combat systems in each of the domains, this JADC2 vision sees assets combined through digital connective “glue” to become a “weapon system” to conduct disaggregated, distributed operations over an entire operational area. This will require treating every platform as a sensor as well as an “effector.” It will require a new battle command architecture and command and control paradigm that enables automatic linking, as does cellular phone technology today. It will also need to transfer data securely, reliably, and seamlessly, without need for human interaction.
The Envisioned Transformation
The overarching goal of actualizing JADC2 with the degree of integration required to achieve a self-forming, self-healing complex into reality will require a significant effort and will not be easy. Every military service will be involved as will every combatant command. It will require overcoming several major obstacles in organization; culture; training; acquisition; and policy. It will require connecting, decision-making, and responding at speed. It will require resilient networks and a degree of sharing among service components and allies not yet achieved. These are numerous and multifaceted challenges that are being addressed across our militaries, services, and combatant commands. However, due to their complexity it will take many years—if not decades—before the ultimate vision of integrated, interdependent, self-forming, self-healing all domain joint and combined operations are a reality. Yet, the threats facing us are growing and demand solutions today. Accordingly, it is time to move out on those elements of JADC2 that can be changed now in order to meet the challenges of the threats we face today.
Each of the service components and combatant commands have well established operating command and control concepts, facilities, and procedures that have proven workable in conflicts of the past. However, each of the variety of C2 architectures that currently exist will require extensive modification in order to survive—much less operate—against the kind of modern threats that have now emerged.
Growing accessibility to information requires the restructure of command and control hierarchies to facilitate rapid engagement of perishable targets and capitalize on our technological capability. Information synthesis and execution authority must be shifted to the lowest possible levels while senior commanders and staffs must discipline themselves to stay at the appropriate level of war.
– David Deptula
A central prerequisite to successful operations in all the domains is control of the aerospace environment. Once established, it facilitates the freedom of action and movement for all other joint and combined forces—without it, effective joint and/or combined operations are not possible. Accordingly, effective command and control of aerospace operations are critical functions that must be a priority. Our ability to command and control (C2) air and space forces is affected by three major elements: threats, technology, and the velocity of information. The changes in these three areas since the design, establishment, and operation of the U.S. Air Force’s air and space operations center (AOC)—the AN/USQ-163 Falconer—have been dramatic and continue to accelerate. Therefore, it is time to determine whether we can achieve success in future operations by evolving our current concepts of operation, organizations, and acquisition processes for modernization, or must we seek fundamental change to each of these elements that affect the current theater air and space control system. Before providing an answer, let’s take a brief look at each of the trends affecting our ability to effectively command and control aerospace operations.
Future Threats and the Operational Environment
Threats
Today, peer threats hold current means of C2 at unacceptable risk when attempting to operate inside the A2/AD environment. For over 30 years we have essentially been on a C2 holiday having the luxury of not being contested in the aerospace domains. Those days are over. Military competitors have accomplished modernization on an unprecedented scale. They have rapidly closed the gap with the U.S., allies, and friendly militaries across a broad spectrum of capabilities including aircraft, spacecraft, missiles, weapons, cyber, command and control, jammers, electronic warfare, data links, and others. Potential adversaries have also studied the American way of war and have determined that it is better to keep us out of their neighborhood rather than face our combat power. They have adopted and are proliferating anti-access and area denial (A2/AD) capabilities designed to deny U.S. and her allies freedom of action. Mitigating these A2/AD capabilities pose significant challenges driving us to operate with greater
risk and farther away from potential areas of conflict.
A2/AD capabilities threaten our ability to command and control air and space operations in three ways. Near peer adversaries can employ kinetic and non-kinetic weapons to deny us communications and intelligence, surveillance, and reconnaissance (ISR) from our space-based assets thereby isolating our forces and blinding our view. Cyber attacks are becoming more sophisticated and can disrupt operations at our well-established combined air and space operations centers. Accurate long-range cruise and ballistic missiles now threaten these facilities that are large, fixed, and vulnerable. As the factory for generating strategy, plans, and the tasking orders for air and space assets, the CAOC has become an extremely lucrative target.
Technology
New technologies are enabling new capabilities to optimize C2 mechanisms to facilitate accomplishing desired effects. We need to think beyond the constraints that traditional culture imposes on new technology. For example, next generation aircraft may be still labeled in traditional nomenclature as fighters, bombers, airlifters, etc., but technologically they have the capability to perform multiple missions due to the miniaturization of sensors, processing power, weapons, energy production, and other capabilities. They are in reality flying “sensor-effectors” that can form the basis of highly resilient networks of redundant nodes and multiple kill paths to minimize the critical system value of current highly centralized and limited C2 nodes—like CAOCs—that an enemy could easily target.
JADC2 will require much time to engineer as it involves a mammoth conversion of existing concepts, capabilities, and service perspectives. However, accelerating these endeavors can be accomplished through rapid evolution of current command and control paradigms.
– David Deptula
This will require leading-edge networking capabilities, assured communications, and different approaches to solving our data bandwidth challenges. For example, to solve the explosion in data growth from advanced sensors, instead of building bigger pipes to transmit all the collected data, increases in processing power now enables the processing of data on-board and the off boarding of only what is of interest to the users. This approach inverts the way we do ISR processing today. Rapid exchange of information is especially important at the forward edge of combat, for the value of actual data is often transitory and diminishes as time and circumstance pass. The development of a technological approach to share information automatically and rapidly among diverse users and across multiple classifications and allied nations will be a key to creating the future force.
The old adage, “Speed is life” is no longer just about flying—it is also about rapidly evolving software tools to fight and win. We have to think outside of the organizational constructs that history has etched into our collective psyche. Network-centric, interdependent, and functionally integrated operations are the keys to future military success.
Velocity of Information
Significant advancements in telecommunications, sensors, data storage, and processing power are emerging every day. As a result, the targeting cycle has evolved from weeks to days to minutes, and from multiple, specialized, and separate aircraft to the ability to “find, fix, and finish” from one aircraft in minutes. Growing accessibility to information requires the restructure of command and control hierarchies to facilitate rapid engagement of perishable targets and capitalize on our technological capability. Information synthesis and execution authority must be shifted to the lowest possible levels while senior commanders and staffs must discipline themselves to stay at the appropriate level of war.
To move beyond large, centralized, static C2 facilities to mobile, distributed C2, with the capability to handle the same volume and diversity of information of a regional CAOC today will require a reappraisal of how we deal with information flow. The two most important aspects of this future capability will be the “command” metamorphosis it will enable through the synchronizing “control” it will provide. The “art of command” will morph to realize Metcalfe law network values (Metcalfe’s law states that the value of a telecommunications network is proportional to the square of the number of connected users of the system). While the “science of control” will continue to apply Moore’s law expanding technology to extend human capacity. The path for optimal growth of both is found through a focus upon gaining and maintaining a decision cycle advantage as the critical path guide.
environment—and that effort must begin now.
The Need for a New Architecture for Aerospace C2—Rapidly
We are now at a juncture where threats, technology, and the velocity of information, require a change in the established architectures to command and control aerospace forces. All the U.S. military services have recognized this and have initiated actions to take appropriate action to develop new concepts of operation for their respective domains. The challenge will be how to assure the integration of each of the individual service concepts of operation into a unified joint all domain command and control architecture. Developed with the idea of creating an ISR, strike, maneuver, and sustainment complex that uses information age technologies to conduct highly interconnected, distributed operations, this “combat cloud” will usher in an entirely different architecture for the conduct of war. The fundamental basis of JADC2 is to push accurate, decision-quality information down to the lowest information node to achieve a desired effect, regardless of service, domain, or platform. The U.S. Air Force approach to this goal is their efforts to design and develop an advanced battle management system (ABMS). However, while the elements of the ABMS have been defined, they have yet to be developed into an executable C2 architecture. To get to the desired end state of the ubiquitous and seamless sharing of information across the battlespace in a secure, reliable, and robust fashion for both JADC2 and ABMS will take many years. Given the rapid evolution of significant threats and the vulnerability of current C2 facilities, modification to the current C2 construct for aerospace forces is required now.
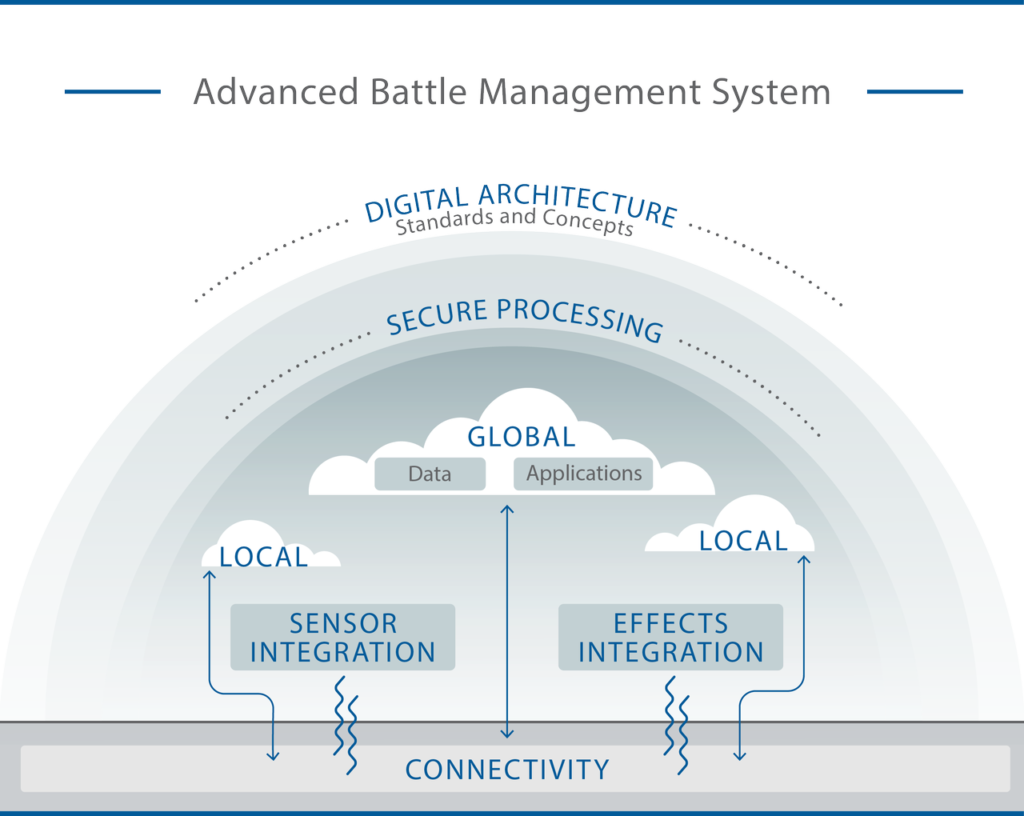
The fundamental basis of JADC2 is to push accurate, decision-quality information down to the lowest information node to achieve a desired effect, regardless of service, domain, or platform.
– David Deptula
What is needed is a new architecture to support an operating concept that actualizes the C2 paradigm that has recently been ensconced in U.S. Air Force Doctrine of centralized command; distributed control; and decentralized execution. No breakthroughs in technology are required to institute a new battle command architecture as the technology already exists to deal with the immediate challenge of distributing C2 functions so that they cannot be eliminated with a few strikes on a few critical C2 nodes.
The U.S. Air Force has been developing a supporting concept of operations to their new doctrine known as agile combat employment or ACE. ACE is a concept that disperses forces and assets to multiple separated locations on short notice to complicate adversary planning. With an appropriate C2 system it can hold adversary targets at risk from many locations that are defensible, sustainable, and relocatable. The details for application of the concept are unique depending on the theater of use, but fundamentally the idea is the same, and C2 is fundamental to the concept’s success.
While the CAOC will remain a viable means to conduct C2 operations during periods of less than major regional conflict, to achieve the objectives of JADC2 we will have to deliver information to warfighters at the edge of the battlespace without having to rely on the traditional CAOC model of hundreds of people organized in stove-piped divisions around segregated mission areas. Accordingly, we need to rapidly evolve beyond the large, centralized CAOC structures we rely on today to a much more agile and dispersible set of processes and C2 structures. At the same time this new architecture must be adaptable to ABMS and JADC2 developments. However, given the slow evolution of these programs, we simply cannot wait to begin changing the architecture for C2 of aerospace forces.
Options for this new architecture are many: build hardened CAOCs and remote the functions to assigned units; distribute the planning functions currently incorporated in COACs among multiple locations and network the resultant plans; create processes and procedures to be executed based on the degree of degradation of connectivity between combat units and their respective command elements by shifting execution authority corresponding to levels of connectivity; and there are many others. Regardless of the option(s) selected for development one thing is certain, we must undertake a determined effort to distribute the C2 functions necessary to assure the effective use of aerospace forces in a contested







